
Praying Mantis An Advanced Memory Resident Attack
Sygnia researchers identified an advanced threat actor targeting high profile US organizations, using nation-state attack methods, and operating in-memory.
While responding to targeted attacks on high-profile organizations in the United States, Sygnia researchers investigated an advanced memory-resident attack commonly associated with nation-state actors.
Key points
- The Sygnia Incident Response team identified an advanced and persistent threat actor, operating almost completely in-memory. Sygnia refers to this threat actor as “Praying Mantis” or TG1021.
- The operators behind the activity targeted Windows internet-facing servers, using mostly deserialization attacks, to load a completely volatile, custom malware platform tailored for the Windows IIS environment.
- The threat actor utilized the access provided using the IIS to conduct additional activity, including credential harvesting, reconnaissance, and lateral movement.
- The Tactics, Techniques and Procedures (TTPs) used by TG1021, bare various similarities to those of “Copy-Paste Compromises” nation-sponsored actor described by the Australian Cyber Security Centre (ACSC).
- Praying Mantis, which has been observed targeting high-profile public and private entities in two major Western markets, exemplifies a growing trend of using nation-state attack methods to target commercial organizations.
- The full report includes the threat actor’s modus operandi, as well as actionable insights, IOCs and guidelines for defending against Praying Mantis Attacks.
Overview
During the past year, Sygnia’s Incident Response team has been responding to a series of targeted cyber intrusion attacks performed by a highly capable and persistent threat actor. The attacks targeted prominent organizations in the U.S. and exploited internet-facing servers to infiltrate their networks.
An advanced, stealthy threat actor
The attack Sygnia identified and responded to was carried out by an advanced and persistent threat actor dubbed “Praying Mantis”, which operates almost completely in-memory.
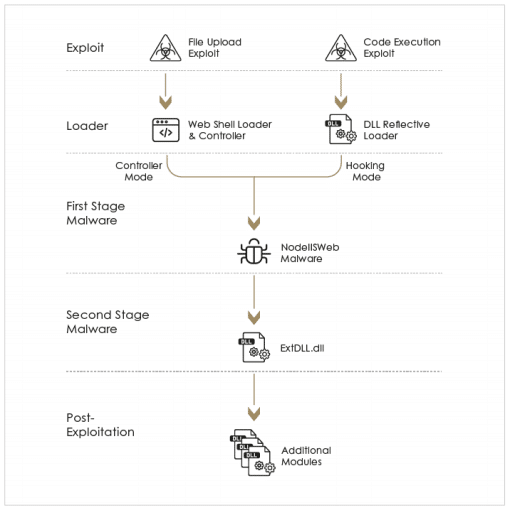
The initial foothold within the network was obtained by leveraging a variety of deserialization exploits targeting Windows IIS servers and vulnerabilities targeting web applications. The activities observed suggest that Praying Mantis is highly familiar with the Windows IIS software and equipped with zero-day exploits.
Praying Mantis utilizes a completely volatile and custom malware framework tailor-made for IIS servers. The core component loaded on to internet-facing IIS servers, intercepts and handles any HTTP request received by the server. The threat actor also uses an additional stealthy backdoor and several post-exploitations modules to perform network reconnaissance, elevate privileges, and move laterally within networks.
The nature of the attack and general modus operandi of the activities suggest that Praying Mantis is an experienced stealthy actor highly aware of OPSEC (operations security). The malware used shows a significant effort to avoid detection by actively interfering with logging mechanisms, successfully evading commercial EDRs, as well as silently awaiting incoming connections rather than connecting back to a C2 channel and continuously generating traffic. Furthermore, Praying Mantis actively removed all disk-resident tools after using the – effectively sacrificing persistency for stealth.
Have we seen this before?
The threat actor’s tactics, techniques, and procedures (TTPs) strongly correlate with the ones described in an advisory published by the Australian Cyber Security Centre (ACSC) in June 2020. The advisory details the activities of a sophisticated state-sponsored actor targeting Australian public and private sector organizations. Specifically, it states: “The Australian Government is currently aware of, and responding to, a sustained targeting of Australian governments and companies by a sophisticated state-based actor. This activity represents the most significant, coordinated cyber-targeting against Australian institutions the Australian Government has ever observed.”
Defending against a Praying Mantis attack
The Sygnia research report contains detailed recommendations on defending networks against this stealthy and sophisticated threat actor.
Continuous forensics activities and timely incident response are essential to identify and effectively defend from attacks by similar threat actors.
In the report we share the threat actor’s modus operandi, in-depth analysis of its capabilities, and provide actionable insights, IOCs and guidelines for defending against Praying Mantis attacks.
Click here for the full report
To learn how to hunt and detect Praying Mantis, click here.

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.



