
Chapter 1 – Introduction
The intricacies of WUDO (Windows Update Delivery Optimization).
Introduction
This set of blog posts was created following extensive research that I conducted on Windows Updates Delivery Optimization (WUDO – or more simply: DO). In these posts, I will lead you through the entire research process, and share some of the guidelines we follow during a research project.
Back when I was a junior researcher, I aspired to constantly improve, and learn new techniques – but I barely found any guides to use that could contribute to my own investigations. Usually, research papers display a final impressive result, without showing how that result was achieved. On the one hand, this is understandable, as research is more of an art than a science, and some processes and practices can be hard to quantify; but on the other hand, we would like to do better: we would like to create research-based articles that can really serve other researchers.
I wrote these articles to portray the nuances involved in this kind of work, and to tell the story of my research. These articles explain my thought processes at the time, show the different options I explored, and don’t try to hide the attempts and directions that were ultimately fruitless.
It is my hope that these articles will give you a glimpse into our approach to such projects and inspire you in your own research.
Do overview
According to Microsoft, “Windows updates, upgrades, and applications can contain packages with large files … Delivery Optimization is a cloud-managed solution that allows clients to download those packages from alternate sources (such as other peers on the network) in addition to the traditional Internet-based servers”.
In other words, Delivery Optimization is a method that Windows machines use to download updates from other Windows machines in the same network or on the internet, instead of directly from Microsoft servers.
We were intrigued by this method, and wanted to understand how Microsoft designed such a system – especially given that it seems to be prone to security issues, and reveals a new potential attack surface. We decided to research Delivery Optimization for two primary reasons: to gain a greater understanding of the mechanism, and to search for security implications and vulnerabilities.
Discovery
Before we get started, I have a confession to make … even as a vulnerability researcher, I too am occasionally tempted to press the snooze button on Windows updates (until the IT department forces a restart of my machine). In a way, it doesn’t matter how much awareness you have of the destructive potential of vulnerabilities inherent in unpatched operating systems – who has the time or energy to close all of their open programs? After running out of delay options and finally succumbing to a Windows update on my home computer, I discovered a section named ‘Delivery Optimization’ that caught my attention:
Surprisingly, the details of this section state that updates and installations can be downloaded from other machines in my local network:
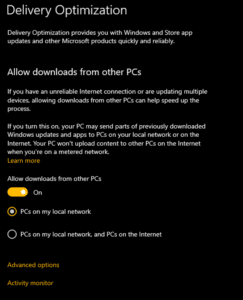
Delving into the settings, you can even see statistics about DO bandwidth:
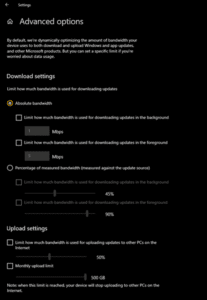
Why do?
Research projects tend to be medium- to long-term projects, ranging from several weeks to multiple months. For this reason, it is crucial to choose worthwhile topics before you become too committed to your chosen research topic.
Delivery optimization raises a number of fascinating questions, and has great potential for vulnerabilities and impact. Some of the questions we formulated were:
- How does this feature work?
- Can I remotely access the update status, and thus detect CVE patching?
- Can I send malicious updates to unsuspecting peers?
- How is the network protocol implemented? Does it avoid the memory corruption and logical vulnerabilities from which such protocols tend to suffer?
We realized that this mechanism could be an extremely powerful attack vector. Taking into consideration the knowledge we gained about it so far, we decided to pour our resources into dissecting DO.
Microsoft documentation
Microsoft has excellent high-level documentation about DO.

But we won’t pointlessly redocument all the available resources on the subject; if you would like to learn more, I recommend these articles:
- Quick introduction: https://support.microsoft.com/en-us/windows/windows-update-delivery-optimization-and-privacy-bf86a244-8f26-a3c7-a137-a43bfbe688e8
- Workflow: https://docs.microsoft.com/en-us/windows/deployment/do/delivery-optimization-workflow
- Longer introduction: https://docs.microsoft.com/en-us/windows/deployment/do/waas-delivery-optimization
- FAQ: https://docs.microsoft.com/en-us/windows/deployment/update/waas-delivery-optimization-faq
- DO API, contains some low-level information: https://docs.microsoft.com/en-us/windows/win32/delivery_optimization/do-reference
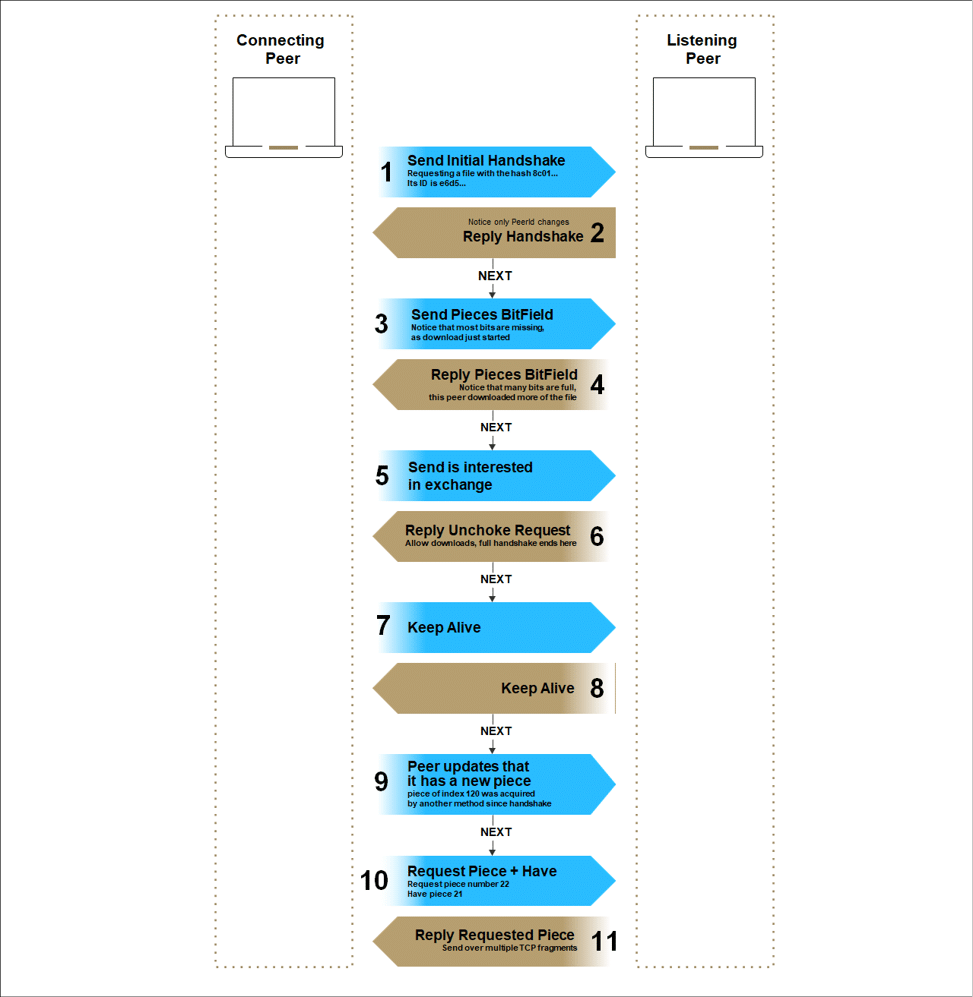
Spoiler alert
The following diagram shows a communication record that we sniffed between two peers conducting a file exchange. You probably have many questions about the flow, and protocol specifications; don’t worry, in the following chapters we’ll give a detailed explanation of how we unveiled the DO protocol, provide full specifications, and explore its possibilities.
What next?
I hope that this brief introduction to Delivery Optimization has piqued your interest. Personally, at this stage, I was thrilled to check out the mechanism.
In the following chapters, we’ll delve into the research, focusing on another subject in each chapter:
- Chapter 2 – Black Box Research
- Chapter 3 – Reversing DoSvc with Ghidra
- Chapter 4 – Network Analysis
- Chapter 5 – Fuzzing
These will be released in the near future, along with technical guides of some of the technologies and techniques used in the research. I encourage you to jump to the following black box chapter, which is released together with this introduction chapter.

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.



